Unveiling the Secrets of Feistel Ciphers: Security Proofs and Cryptanalysis

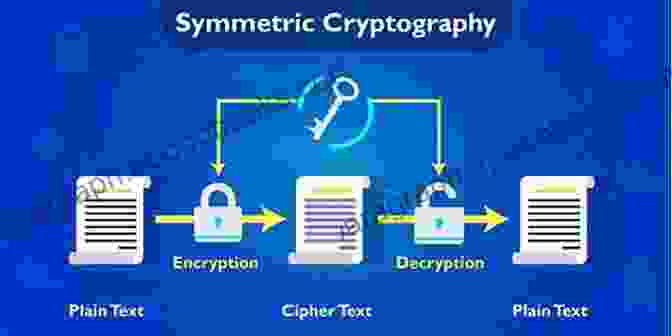
In the realm of cryptography, Feistel ciphers reign supreme as one of the most prevalent and influential constructions of symmetric block ciphers. Their widespread adoption in industry-standard algorithms like DES and AES underscores their significance in safeguarding sensitive information.
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |
This comprehensive guide dives deep into the intricacies of Feistel ciphers, unraveling their intricate security proofs and cryptanalytic techniques. We embark on an illuminating journey to decipher the theoretical foundations that underpin these ingenious cryptographic constructs.
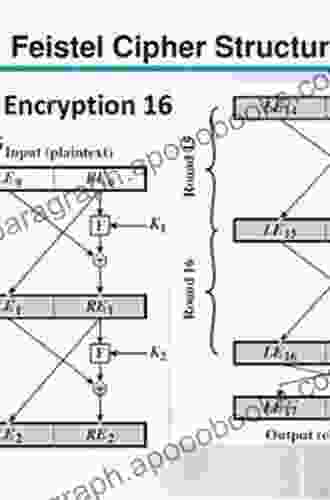
Feistel Cipher Structure and Operation
Feistel ciphers operate on the principle of iteratively applying a round function, comprising two sub-functions: a substitution layer and a permutation layer. This iterative process transforms the input plaintext block into an output ciphertext block.
The substitution layer typically employs S-boxes, non-linear functions that introduce diffusion into the cipher. The permutation layer, on the other hand, permutes the bits of the data, enhancing confusion. The number of rounds, along with the choice of S-boxes and permutation functions, significantly influences the cipher's security strength.
Security Proofs for Feistel Ciphers
The security of Feistel ciphers rests on a solid mathematical foundation. Researchers have meticulously developed proofs to demonstrate their resistance to various cryptanalytic attacks.
- Luby-Rackoff Theorem: This fundamental theorem establishes a connection between the security of a Feistel cipher and the security of its underlying round function. It asserts that if the round function is a pseudorandom function (PRF),then the Feistel cipher is also a PRF.
- Lai-Massey Theorem: This theorem provides a more precise bound on the number of rounds required for a Feistel cipher to achieve a certain level of security. It states that n rounds of a Feistel cipher with an n-bit block size provide at least 2^n/2 security bits against certain attacks.
Cryptanalytic Techniques for Feistel Ciphers
Despite their robust security proofs, Feistel ciphers are not immune to cryptanalytic attacks. Cryptographers have devised ingenious techniques to exploit potential weaknesses in these ciphers.
- Differential Cryptanalysis: This technique aims to identify pairs of plaintext inputs that produce a specific difference in the ciphertext. By analyzing these differences, attackers can deduce information about the cipher's internal structure.
- Linear Cryptanalysis: This technique involves constructing linear equations based on the XOR of plaintext and ciphertext bits. By solving these equations, attackers can recover secret key bits.
Applications and Significance of Feistel Ciphers
Feistel ciphers have found widespread applications in the field of cryptography. Their versatility and proven security make them the preferred choice for a multitude of cryptographic applications.
- Data Encryption Standard (DES): DES, developed in the 1970s, is a classic example of a Feistel cipher. It employed a 56-bit key and was used extensively for encrypting sensitive data.
- Advanced Encryption Standard (AES): AES, adopted in 2001, is a more robust Feistel cipher with a 128-, 192-, or 256-bit key. It is currently the most widely used block cipher globally.
- Other Applications: Feistel ciphers are also employed in a variety of other cryptographic applications, such as hash functions, message authentication codes, and stream ciphers.
Feistel ciphers stand as a testament to the ingenuity and mathematical rigor that underpin the field of cryptography. Their security proofs provide a solid foundation for their widespread adoption in industry-standard algorithms. However, the continuous evolution of cryptanalytic techniques necessitates ongoing research to ensure the continued security of these indispensable cryptographic constructs.
As the frontiers of cryptography expand, Feistel ciphers will undoubtedly continue to play a pivotal role in safeguarding sensitive information and ensuring the integrity of our digital communications.
Learn more:
- Wikipedia: Feistel Cipher
- NIST: Data Encryption Standard (DES)
- NIST: Advanced Encryption Standard (AES)
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia John Marsh
John Marsh Helen Hossley
Helen Hossley G Alan Tarr
G Alan Tarr Eric Brunsell
Eric Brunsell Marguerite Sauvage
Marguerite Sauvage Frank Furedi
Frank Furedi Sakar Pudasaini
Sakar Pudasaini Eric Barker
Eric Barker Enver Hoxha
Enver Hoxha Floyd D Beachum
Floyd D Beachum Stephen Hawkins
Stephen Hawkins Felicia Guy Lynch
Felicia Guy Lynch Franz Wright
Franz Wright Isaac M Hamm Iii
Isaac M Hamm Iii Ermelinda Makkimane
Ermelinda Makkimane Frank Javier Garcia Berumen
Frank Javier Garcia Berumen Eva Seligman
Eva Seligman Evan Woodbery
Evan Woodbery Fiona D Arcy Stewart
Fiona D Arcy Stewart Grace Burrowes
Grace Burrowes
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Leon FosterThe Tale of Peddler Some Monkeys and Their Monkey Business: A Reading Rainbow...
Leon FosterThe Tale of Peddler Some Monkeys and Their Monkey Business: A Reading Rainbow...
 David PetersonThis Is the Most Heartwarming, Page-Turning, and Emotional Historical Novel...
David PetersonThis Is the Most Heartwarming, Page-Turning, and Emotional Historical Novel... Kevin TurnerFollow ·7.9k
Kevin TurnerFollow ·7.9k George BellFollow ·8.1k
George BellFollow ·8.1k Neil GaimanFollow ·4.7k
Neil GaimanFollow ·4.7k Vladimir NabokovFollow ·17.4k
Vladimir NabokovFollow ·17.4k Warren BellFollow ·16.5k
Warren BellFollow ·16.5k Hank MitchellFollow ·13.3k
Hank MitchellFollow ·13.3k Thomas HardyFollow ·9.9k
Thomas HardyFollow ·9.9k W. Somerset MaughamFollow ·17.9k
W. Somerset MaughamFollow ·17.9k

 Stephen Foster
Stephen Foster26 Projects And Personalities From The Knitting...
Knitting is a...

 Lucas Reed
Lucas ReedThe Lone Star Hijack: How Texas Sabotaged the American...
In her explosive new...

 Ignacio Hayes
Ignacio Hayes"Bars for Days": Unlocking the Lyrical Brilliance of Mic...
A Journey into...

 Edmund Hayes
Edmund HayesNew Life, No Instructions: A Memoir of Unforeseen...
A Riveting Tale of Loss,...

 W.B. Yeats
W.B. YeatsUnveiling the Intricate Cultural Fabric of Mainland China...
In the tapestry of human history,...

 Anthony Burgess
Anthony BurgessGestalt Counselling In Nutshell: A Comprehensive Guide...
Gestalt counselling is a therapeutic...
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |